Facebook and MySpace security: backdoor wide open, millions of accounts exploitable
Facebook and MySpace fixed this quickly after being notified.
As a application developer on Facebook, I usually run into certain walls that limit my application functionality. But I don't give up easily, and only recently I found a solution to one of my function limitations. Surprisingly, when looked into more carefully my solution allowed full access and control to the Facebook user account that accessed my application. Did I mention this would also be untraceable since exploit actions would happen from the users IP and own domain cookie?
Lets walk through it along some clarifying images. Flash applications run on a users' computer. A Flash application is able to load data into its environment. This is done by a request of the application, where the user loads a certain URL. Luckily - just with browser AJAX requests- a flash application hosted on domain X is unable to open a file on domain Y. If this would be possible, domain X is able to access content on domain Y, and when the user is logged in on domain Y retrieve and post back any personal data.
In certain cases this could limit a flash application capabilities. A relevant example: an application wants to display public Facebook user thumbnails. The application is on domain X, the thumbnails on domain facebook.com. To resolve such issues, Adobe (Flash's developers) introduced a "crossdomain.xml" file which could allow certain domains accessing another domain, leading to cross domain access by certain or all domains.
While indeed Facebook locked the front door from any non-facebook domain access via Flash, a simple subdomain change allowed any flash application (domain="*") to access it's domain data:.
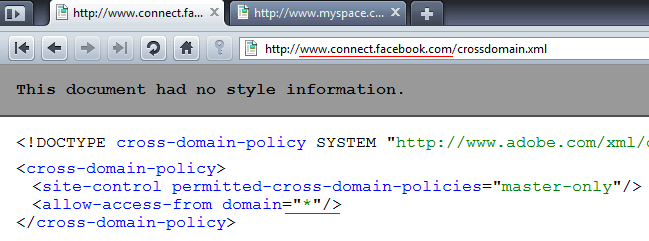
This wouldn't be a big deal if the subdomain only hosts images, but unfortunately this domain hosts the whole Facebook property, including a facebook user session.
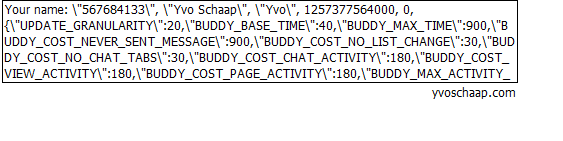
If you have auto-login enabled on facebook, you might recognize your fullname [update: its a screen cap now] in the snippet above (and the keys to do actions from the accounts credentials).
A huge problem that leads to full access and control of a user account whom has "auto login" enabled, and who hasn't?
But how does MySpace fit in this story? You would be surprised if I found a similar back door on not one, but two of the top 10 websites online, right? Well a quick look at the MySpace crossdomain.xml file shows again a locked door, except for one element: the domain farm.sproutbuilder.com was enabled to access myspace.com data.
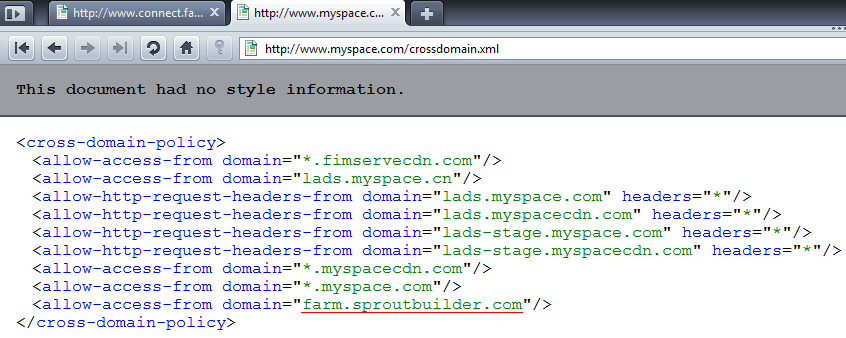
A look at "sproutbuilder" showed a application builder (which indeed has a module able to load MySpace data: news updates) but more disturbing an upload function allows anybody uploading ".swf" files, the file extension of Flash applications. The location of the uploaded file? farm.sproutbuilder.com [exploit closed], exactly the domain that is allowed access to MySpace data.
You don't need much time to think of all the ways this could be exploited. All what has to happen is a active session, or a "auto login"-cookie and a URL which hosts a exploiting Flash file. For example when accessed, a automatic "post update" could be made, that would lure friends of the user to access the exploit URL, and the exploit would spread virally. An more invasive and hidden exploit could harvest all the users personal photo's, data and messages to a central server without any trace, and there is no reason why this wouldn't be happening already with both Facebook and MySpace data.
News item featured in various publications:
